This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful strategy...
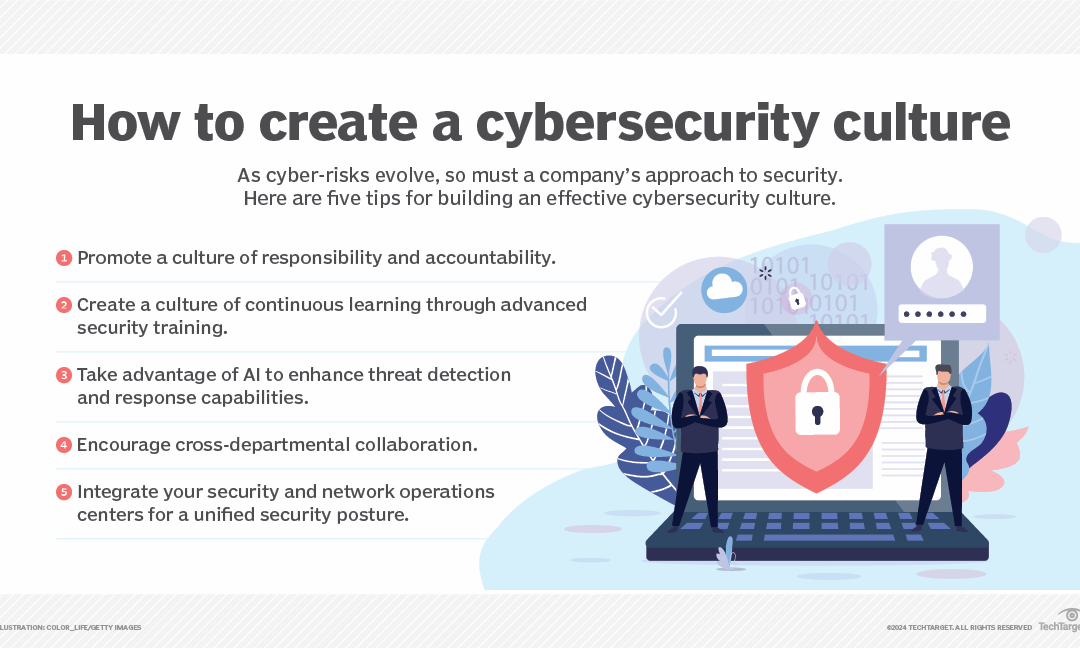

This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful strategy...

While home health agencies face distinct health IT challenges, collaboration and innovation are crucial for overcoming these...

The umbrella term malware is one of the greatest cybersecurity threats enterprises face. Learn about 12 common types of malware...

Originally Published on TechTarget.com by Sharon Shea, Executive Editor and Alexander S. Gillis, Technical Writer and Editor...
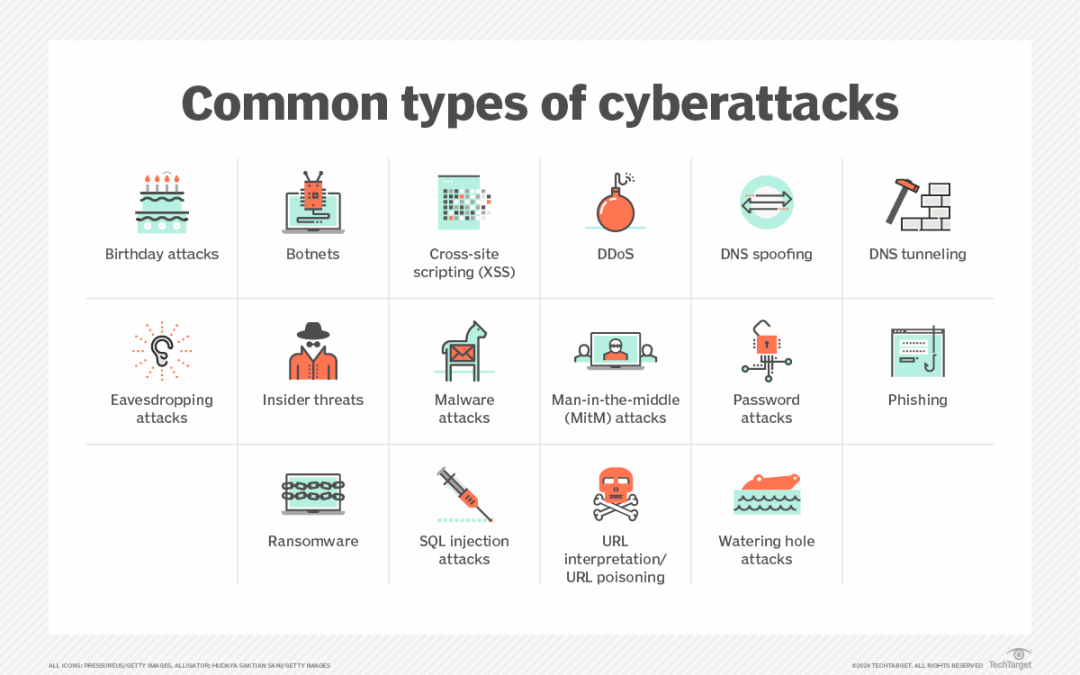
To stop cyberattacks, companies must understand how they're being attacked. Here are the most damaging types of cyberattacks and...
Know thine enemy — and the common security threats that can bring an unprepared organization to its knees. Learn what these threats are and how to prevent them.
By TechTarget Contributor Published: 29 Jan 2024
Although security threats, security events and security incidents are related, in the world of cybersecurity, these terms have different meanings.
A security threat is a malicious act that aims to corrupt or steal data or disrupt an organization’s systems or the entire organization. A security event refers to an occurrence during which company data or its network may have been exposed. An event that results in a data or network breach is called a security incident.
As cybersecurity threats continue to evolve and become more sophisticated, enterprise IT must remain vigilant when protecting their data and networks. To do that, they must first understand the types of security threats and potential attacks they’re up against.
Below are the top 10 types of information security threats that IT teams need to know.
An insider threat occurs when individuals close to an organization who have authorized access to its network intentionally or unintentionally misuse that access to affect the organization’s critical data or systems negatively.
Careless employees who don’t comply with their organizations’ business rules and policies cause insider threats. For example, they may inadvertently email customer data to external parties, click on phishing links in emails or share their login information with others. Contractors, business partners and third-party vendors are the source of other insider threats.
Some insiders intentionally bypass security measures out of convenience or ill-considered attempts to become more productive. Malicious insiders intentionally elude cybersecurity protocols to delete data, steal data to sell or exploit later, disrupt operations or otherwise harm the business.
The list of things organizations can do to minimize the risks associated with insider threats includes the following:
Viruses and worms are malicious software programs (malware) aimed at destroying an organization’s systems, data and network. A computer virus is a malicious code that replicates by copying itself to another program, system or host file. It remains dormant until someone knowingly or inadvertently activates it, spreading the infection without the knowledge or permission of a user or system administration.
A computer worm is a self-replicating program that doesn’t have to copy itself to a host program or require human interaction to spread. Its main function is to infect other computers while remaining active on the infected system. Worms often spread using parts of an OS that are automatic and invisible to the user. Once a worm enters a system, it immediately starts replicating itself, infecting computers and networks that aren’t adequately protected.
To reduce the risk of these types of information security threats caused by viruses or worms, companies should install antivirus and antimalware software on all their systems and networked devices and keep that software up to date.
In addition, organizations must train users not to download attachments or click on links in emails from unknown senders and to avoid downloading free software from untrusted websites. Users should also be very cautious when they use P2P file-sharing services and they shouldn’t click on ads, particularly ads from unfamiliar brands and websites.
A botnet is a collection of Internet-connected devices, including PCs, mobile devices, servers and IoT devices that are infected and remotely controlled by a common type of malware.
Typically, the botnet malware searches for vulnerable devices across the internet. The goal of the threat actor creating a botnet is to infect as many connected devices as possible, using the computing power and resources of those devices for automated tasks that generally remain hidden from the users of the devices.
The threat actors — often cybercriminals — that control these botnets use them to send email spam, engage in click fraud campaigns and generate malicious traffic for distributed denial-of-service attacks.
Organizations have several ways to prevent botnet infections:
In a drive-by download attack, malicious code is downloaded from a website via a browser, application or integrated OS without a user’s permission or knowledge. A user doesn’t have to click on anything to activate the download. Just accessing or browsing a website can start a download.
Cybercriminals can use drive-by downloads to inject banking Trojans, steal and collect personal information as well as introduce exploit kits or other malware to endpoints.
One of the best ways a company can prevent drive-by download attacks is to regularly update and patch systems with the latest versions of software, applications, browsers and OSes. Users should also be warned to stay away from insecure websites. Installing security software that actively scans websites can help protect endpoints from drive-by downloads.
Phishing attacks are a type of information security threat that employs social engineering to trick users into breaking normal security practices and giving up confidential information, including names, addresses, login credentials, Social Security numbers, credit card information and other financial information.
In most cases, hackers send out fake emails that look as if they’re coming from legitimate sources, such as financial institutions, eBay, PayPal — and even friends and colleagues.
In phishing attacks, hackers attempt to get users to take some recommended action, such as clicking on links in emails that take them to fraudulent websites that ask for personal information or install malware on their devices. Opening attachments in emails can also install malware on users’ devices that are designed to harvest sensitive information, send out emails to their contacts or provide remote access to their devices.
Enterprises should train users not to download attachments or click on links in emails from unknown senders and to avoid downloading free software from untrusted websites.
In a distributed denial-of-service (DDoS) attack, multiple compromised machines attack a target, such as a server, website or other network resource, making the target inoperable. The flood of connection requests, incoming messages or malformed packets forces the target system to slow down or to crash and shut down, denying service to legitimate users or systems.
To help prevent DDoS attacks, companies should take the following steps:
In a ransomware attack, the victim’s computer is locked, typically by encryption, which keeps the victim from using the device or data that’s stored on it. To regain access to the device or data, the victim has to pay the hacker a ransom, typically in a virtual currency such as Bitcoin. Ransomware can be spread via malicious email attachments, infected software apps, infected external storage devices and compromised websites.
To protect against ransomware attacks, users should regularly back up their computing devices and update all software, including antivirus software. Users should avoid clicking on links in emails or opening email attachments from unknown sources. Victims should do everything possible to avoid paying ransom.
Organizations should also couple a traditional firewall that blocks unauthorized access to computers or networks with a program that filters web content and focuses on sites that may introduce malware. In addition, limit the data a cybercriminal can access by segregating the network into distinct zones, each of which requires different credentials.
An exploit kit is a programming tool that enables a person without any experience writing software code to create, customize and distribute malware. Exploit kits are known by a variety of names, including infection kits, crimeware kits, DIY attack kits and malware toolkits. Cybercriminals use these toolkits to attack system vulnerabilities to distribute malware or engage in other malicious activities, such as stealing corporate data, launching denial of service attacks or building botnets.
To guard against exploit kits, an organization should deploy antimalware software as well as a security program that continually evaluates if its security controls are effective and provide protection against attacks.
Enterprises should also install antiphishing tools because many exploit kits use phishing or compromised websites to penetrate the network.
An advanced persistent threat (APT) is a targeted cyberattack in which an unauthorized intruder penetrates a network and remains undetected for an extended period of time. Rather than causing damage to a system or network, the goal of an APT attack is to monitor network activity and steal information to gain access, including exploit kits and malware.
Cybercriminals typically use APT attacks to target high-value targets, such as large enterprises and nation-states, stealing data over a long period.
Detecting anomalies in outbound data may be the best way for system administrators to determine if their networks have been targeted.
Indicators of APTs include the following.
To combat this type of information security threat, an organization should also deploy a software, hardware or cloud firewall to guard against APT attacks.
Organizations can also use a web application firewall to detect and prevent attacks coming from web applications by inspecting HTTP traffic.
Malvertising is a technique cybercriminals use to inject malicious code into legitimate online advertising networks and web pages. This code typically redirects users to malicious websites or installs malware on their computers or mobile devices. Users’ machines may get infected even if they don’t click on anything to start the download.
Cybercriminals may use malvertising to deploy a variety of moneymaking malware, including crypto-mining scripts, ransomware and banking Trojans.
Some of the websites of well-known companies, including Spotify, The New York Times and the London Stock Exchange, have inadvertently displayed malicious ads, putting users at risk.
To prevent malvertising, ad networks should add validation; this reduces the chances a user could be compromised. Validation could include vetting prospective customers by requiring legal business paperwork. Requiring two-factor authentication. Scanning potential ads for malicious content before publishing an ad; or converting Flash ads to animated GIFs or other types of content.
To mitigate malvertising attacks, web hosts should periodically check their websites from an unpatched system, and monitor that system to detect any malicious activity. The web hosts should disable any malicious ads.
To reduce the risk of malvertising attacks. Enterprise security teams should be sure to keep software and patches up to date as well as install network antimalware tools.
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit...
This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful...
While home health agencies face distinct health IT challenges, collaboration and innovation are crucial for overcoming...