Why Your Business Needs Cybersecurity More Than Ever? In today's hyper-connected digital world, cybersecurity is no longer a...


Why Your Business Needs Cybersecurity More Than Ever? In today's hyper-connected digital world, cybersecurity is no longer a...

Worried about being a target for phishing attacks? Protect your company today!

Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit card...
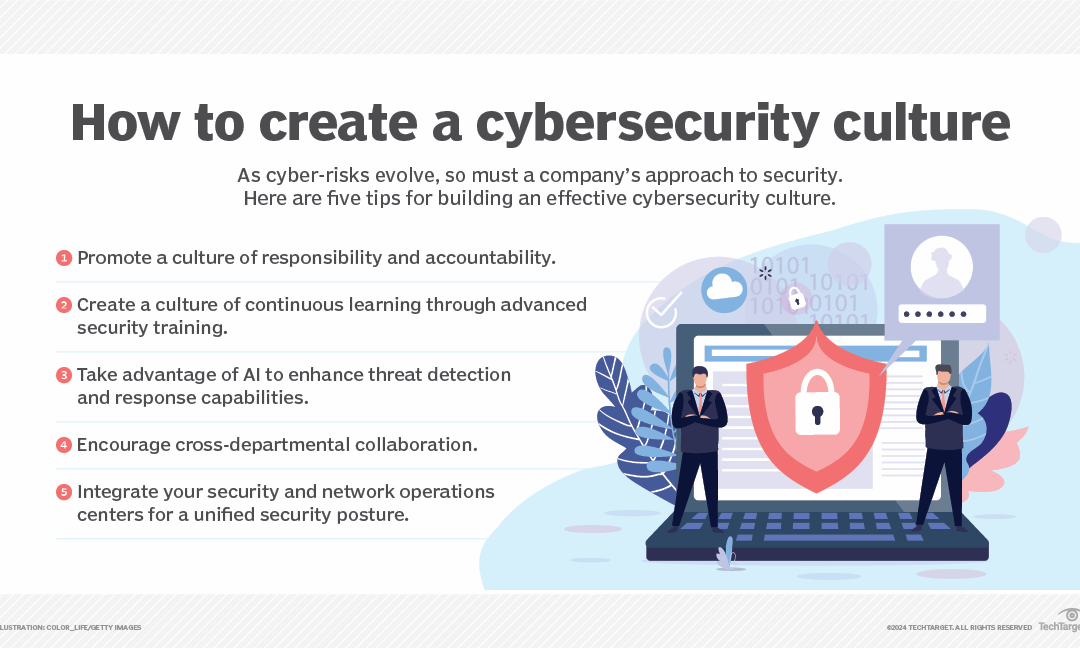
This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful strategy...
Cybersecurity Threats: Not Just an IT Issue — A Business Risk
What looks like a harmless IT issue can quickly spiral into a full-blown crisis. A missed security update. A suspicious email ignored. An ex-employee still having system access. These may all seem like minor IT issues—but in today’s threat landscape, they can become business-ending events.
A cyberattack is no longer just an IT issue. It’s an attack on your brand, your revenue, and your customers’ trust.
At Western I.T., we specialize in identifying what others dismiss as small IT issues—because we know they’re often the first signs of much larger threats. In this post, we break down the three most common cyber threats that often begin as simple IT issues and reveal why addressing them is more than just an IT task—it’s a business survival strategy.
What is it?
Phishing is one of the most common forms of cyberattacks, and it’s often the starting point for more serious breaches. These attacks involve deceptive emails, fake login screens, and fraudulent invoices designed to trick employees into sharing passwords or clicking malicious links.
Common Scenarios:
These attacks aren’t random—they’re targeted, and your employees are the entry point.
Why It Matters:
One wrong click from one employee can compromise the entire network. That click could expose confidential business data, give hackers access to your systems, or lead to internal fraud. In fact, according to global statistics, over 90% of breaches start with a phishing attempt.
What is it?
Ransomware is a form of malicious software that encrypts your files or systems, locking you out until a ransom is paid. These attacks are often delivered through phishing emails or infected downloads and can cripple a business within minutes.
How It Happens:
Why It Matters:
Ransomware doesn’t just disrupt—it destroys trust. Clients may hesitate to share information with you again, compliance fines may follow, and your operations can be frozen for days or weeks. Paying the ransom doesn’t guarantee recovery—and rebuilding from backups can be costly if not done right.
Downtime = lost revenue + lost confidence + lost time.
What is it?
With the rise of remote work, cloud platforms, and shared devices, more businesses than ever are vulnerable to weak login security. Attackers exploit reused passwords, unsecured accounts, and outdated user permissions to gain quiet but complete access.
Real-World Examples:
Why It Matters:
Unlike obvious cyberattacks, credential theft can go undetected for months. Hackers use stolen credentials to navigate systems as legitimate users—collecting data, exfiltrating information, or preparing for a larger attack.
It’s easy to think cybersecurity is something your IT provider “just handles,” but in reality, protecting your business from cyber threats requires a collaborative and proactive approach.
Here’s what we recommend:
At Western I.T., our WIT Protect and WIT365 packages offer layered, real-time defense against malware, ransomware, and phishing. We go beyond antivirus—we implement cloud backups, access control, cyberattack remediation, and 24/7 monitoring.
Whether you’re a growing business with limited IT resources or an established firm looking to strengthen your defenses, we’re here to help.
Let us shield your business with enterprise-grade cybersecurity solutions designed for the real-world threats medium-sized businesses face every day.
Stay Safer, One Email at a Time: Introducing Our New AI-Powered Email Scanner In today's rapidly evolving digital...
Why Your Business Needs Cybersecurity More Than Ever? In today's hyper-connected digital world, cybersecurity is no...
Worried about being a target for phishing attacks? Protect your company today!